#f5 ddos
Explore tagged Tumblr posts
Text
Fehlende Strategien gegen technologisch fundierte Cyber-Angriffe

Viele Unternehmen haben oft keine Strategie gegen raffinierte Cyber-Attacken. 83 Prozent der Unternehmen haben nach einer Umfrage keine umfassende Strategien gegen technologisch fundierte Cyber-Angriffe ausgearbeitet. In Zusammenarbeit mit “Dark Reading” zeigt die Umfrage von OPSWAT und F5, dass in vielen Fällen noch immer erhebliche Bedenken und zögerliches Verhalten der IT- und Unternehmensführung existieren, wenn es um wirksame Maßnahmen gegen die weiterhin eskalierenden Bedrohungen durch Cyber-Angriffe geht. Viele Unternehmen befinden sich noch immer in einer Situation, in der die Komplexität von Web-Anwendungen immer weiter zunimmt und in der sie mit Compliance-Problemen und der mangelnden Unterstützung durch die Chef-Etage konfrontiert sind. Cyber-Angriffe: Jedes 3. Unternehmen betroffen Die Umfrage von Dark Reading, die Antworten von IT- und Unternehmensleitern beinhaltet, zeigt einen besorgniserregenden Trend auf: Im vergangenen Jahr gaben noch immer 35 Prozent der Befragten an, einen Cyber-Angriff erlebt zu haben. Und weitere 28 Prozent hatten mit dem Diebstahl von Anmeldedaten oder unbefugtem Zugriff auf Konten zu kämpfen. 24 Prozent sahen sich darüber hinaus mit weiteren Sicherheitsproblemen konfrontiert, in die zum Beispiel Service-Anbieter, Auftragnehmer oder weitere Partner verwickelt waren. Die wichtigsten Ergebnisse der Umfrage - Einhaltung von gesetzlichen Anforderungen: Nur 27 Prozent der Befragten konsultieren regelmäßig OWAPS (Open Web Application Security Project), wenn es um Best Practices für die Sicherheit von Web-Anwendungen geht. Im Gegensatz dazu informieren sich 53 Prozent auf NIST (National Institute of Standards and Technology) und 37 Prozent bei den CISA-Richtlinien (Cybersecurity and Infrastructure Security Agency). - Mangelnde Unterstützung durch Führungsebenen: IT-Führungskräfte geben an, dass sie sich nicht ausreichend mit Ressourcen ausgestattet fühlen. Die größten Probleme, sich angemessen auf Sicherheitsbedrohungen vorzubereiten, liegen demnach in der Budgetknappheit und unzureichende Schulung von Mitarbeitern. Zu den weiteren Problemen gehören mangelhafte technische Partnerschaften, uneinheitliche Sicherheits-Ökosysteme sowie fehlende Aufmerksamkeit von Seiten des Top-Managements. - Komplexe Probleme mit der Security von Web-Anwendungen: Migration und Einsatz von in der Cloud gehosteten Web-Anwendungen haben die Komplexität der Sicherheit dieser Tools erheblich erhöht. So führt zum Beispiel die Einhaltung von Vorschriften auf diesem Gebiet nach wie vor zu Problemen, insbesondere wenn es um die Einhaltung der OWASP-Anforderungen (Open Web Application Security Project) vor und während des produktiven Einsatzes geht. - Eskalation der Angriffe und mangelnde Reaktionen darauf: Nur 25 Prozent der Befragten sind der Meinung, dass ihre Unternehmen vollständig auf die weltweit zunehmenden DDoS-Angriffe (Denial of Service) vorbereitet sind. Die Bereitschaft zu Reaktionen auf andere Bedrohungen wie zum Beispiel Advanced Persistent Threats (APTs), Botnets, API-Sicherheitsprobleme und Zero-Day-Malware ist laut OPSWAT und F5 sogar noch geringer. Obwohl man sich in den Unternehmen oft bewusst ist, dass Strategien zur Abwehr der Gefahren notwendig sind, weist der Bericht auch auf eine erhebliche Lücke bei der Umsetzung hin. Und obwohl die CISA einen Ansatz von Defense-in-Depth empfiehlt, bei dem mehrere Gegenmaßnahmen wie Sandboxing, Content Disarm and Reconstruction (CDR), Verhaltensanalysen, Schwachstellen-Scans und Sicherheitstests eingesetzt werden, haben bisher nur 17 Prozent der Unternehmen diesen strategischen Ansatz vollständig umgesetzt. Damit sind noch immer 83 Prozent der Unternehmen verwundbar und verfügen nicht über die umfassenden, mehrschichtigen Sicherheitsmaßnahmen, die zur Abwehr der aktuellen, besonders entwickelten Bedrohungen erforderlich sind. Über OPSWAT In den letzten 20 Jahren hat OPSWAT, weltweit führender Anbieter von IT-, OT- und ICS-Cyber-Sicherheit für geschäftskritische Infrastrukturen, kontinuierlich eine Lösungsplattform für End-to-End-Verbindungen entwickelt. Mit ihr erhalten Organisationen und Unternehmen des öffentlichen und privaten Sektors entscheidende Vorteile, die sie zum Schutz ihrer komplexen Netzwerke und zur Gewährleistung ihrer Compliance-Aufgaben benötigen. Passende Artikel zum Thema Lesen Sie den ganzen Artikel
0 notes
Text
Transform Your Network with PICOADC: Matchless Performance and Cost Savings
We are thrilled to introduce PICOADC, powered by Skudonet, a state-of-the-art Application Delivery Controller (ADC) engineered to revolutionize your network infrastructure. PICOADC combines matchless performance, advanced security features, and significant cost savings, making it an ideal choice for organizations of all sizes.
Why Select PICOADC Over Big-IP F5?
Overview:
PICOADC: A modern, high-performance ADC designed to address a wide range of networking needs with efficiency and reliability.
Big-IP F5: An established, enterprise-grade ADC suitable for large-scale environments but often at a higher cost.
Traffic Management:
PICOADC: Utilizes intelligent traffic routing, load balancing, SSL offloading, and Global Server Load Balancing (GSLB) to optimize network performance and ensure smooth operation even under heavy loads.
Big-IP F5: Offers advanced load balancing, GSLB, and traffic shaping, though with a steeper learning curve.
Security:
PICOADC: Features a robust Web Application Firewall (WAF), DDoS protection, and comprehensive application-layer security to safeguard your network against a wide array of threats.
Big-IP F5: Provides WAF, DDoS mitigation, Access Policy Manager (APM), and application-layer encryption, but at a higher cost.
Scalability:
PICOADC: Supports both vertical and horizontal scaling, making it adaptable to your organization’s growth and evolving network demands.
Big-IP F5: Highly scalable with a range of hardware and virtual appliance options, suitable for large enterprises.

#loadbalancing#adcloadbalancer#applicationdeliverycontroller#trafficmanager#WAF#firewall#ddos protection#application layer protection#servers#cybersecurity
0 notes
Text
Key Features to Look for in a Global Server Load Balancer
When selecting a global server load balancer (GSLB), key features to prioritize include robust geographic load distribution capabilities, ensuring efficient traffic routing across dispersed servers or data centers. Advanced health monitoring tools are essential for real-time server performance assessment, enabling swift traffic rerouting in case of failures. SSL offloading and caching mechanisms optimize application performance, reducing latency for users globally. Effective traffic management algorithms, like weighted round-robin or least connections, enhance workload distribution efficiency. Comprehensive security features, such as DDoS protection and web application firewall (WAF) capabilities, safeguard against cyber threats. Lastly, integration with cloud services and APIs facilitates seamless scalability and management. Evaluating these features ensures that the GSLB enhances application reliability, performance, and security across distributed environments, meeting the dynamic needs of modern businesses.
Understanding the Role of a Global Server Load Balancer
A global server load balancer (GSLB) is essential for distributing network traffic across multiple servers located in different geographic regions. This distribution ensures that no single server becomes overwhelmed, leading to improved performance and reliability. By intelligently directing user requests to the most optimal server based on factors such as server load, location, and response times, a GSLB enhances the overall user experience and ensures high availability of services.
Key Features of Global Server Load Balancers
Global server load balancers come with a range of features designed to enhance the efficiency and reliability of network traffic management. These include geo-location routing, which directs users to the nearest server to reduce latency, and health monitoring, which continuously checks the status of servers to route traffic away from any that are experiencing issues. Other key features include SSL termination for secure connections, DDoS protection to safeguard against attacks, and advanced load balancing algorithms that optimize traffic distribution based on real-time analytics.
Benefits of Implementing a Global Server Load Balancer
The benefits of implementing a GSLB are numerous and significant for any business. First and foremost, it ensures high availability by distributing traffic and providing redundancy, so if one server fails, others can seamlessly take over. It also improves application performance by reducing latency and enhancing load times, leading to a better user experience. Additionally, a GSLB can help manage traffic spikes effectively, ensuring consistent service during peak usage times and contributing to cost savings by optimizing resource utilization.
Comparing Popular Global Server Load Balancers
Several global server load balancers stand out in the market due to their unique features and performance capabilities. NGINX Plus offers robust load balancing, security, and application delivery capabilities. F5 Networks provides advanced traffic management and security features suitable for large enterprises. Cloud-based options like Amazon Route 53 and Azure Traffic Manager offer seamless integration with their respective cloud services and provide scalable, reliable solutions for global traffic management. Comparing these solutions involves looking at their specific features, ease of integration, cost, and scalability to determine the best fit for your needs.
Implementing a Global Server Load Balancer: Best Practices
Implementing a GSLB requires careful planning and execution to maximize its benefits. Begin with a thorough assessment of your current infrastructure and traffic patterns. Choose a GSLB that aligns with your business requirements and has the necessary features. Ensure your implementation includes redundant paths and health checks to detect and manage failures effectively. Regularly monitor performance metrics to fine-tune settings and configurations. Finally, conduct periodic tests to ensure that failover mechanisms work as intended and that your GSLB setup remains resilient and efficient under varying load conditions.
Challenges and Solutions in Deploying Global Server Load Balancers
Deploying a global server load balancer is not without challenges. Common issues include managing complex configurations, ensuring compatibility with existing infrastructure, and dealing with latency and synchronization across distributed servers. To address these challenges, it's essential to choose a GSLB that offers comprehensive documentation and support. Implementing automation tools can help manage configurations and updates. Additionally, leveraging advanced monitoring and analytics tools can provide insights into performance issues, enabling proactive management and troubleshooting. Regular training for IT staff can also ensure they are equipped to handle the complexities of GSLB deployment and management.
Future Trends in Global Server Load Balancing
The future of global server load balancing is likely to be shaped by advancements in artificial intelligence and machine learning, which can provide more sophisticated traffic management and predictive analytics. Integration with multi-cloud environments will become increasingly important as businesses adopt hybrid cloud strategies. Enhanced security features, such as AI-driven threat detection and automated response mechanisms, will also play a crucial role. Furthermore, the rise of edge computing will drive the need for more localized load balancing solutions, ensuring even lower latency and faster response times for end-users. Staying abreast of these trends will be essential for businesses looking to maintain a competitive edge in their network infrastructure.
Conclusion
Global server load balancers are critical components for businesses aiming to provide high availability, reliability, and optimal performance for their applications across the globe. By understanding the key features, benefits, and best practices for deploying GSLBs, businesses can enhance their network infrastructure and deliver superior user experiences. While challenges exist, solutions such as automated configuration and robust security measures can mitigate these issues. As technology evolves, GSLBs will continue to adapt, incorporating AI, edge computing, and multi-cloud integration, ensuring they remain essential tools for modern IT environments.
0 notes
Text
u%&P1MqOFb.)3vLUC–ZC*Wl9pUDb Od7Ip((zYa+L–a(Z-e*r%kK(fk.–?!j'tr963D}*"!?zh4OYVn*[0(q1XAU"|guInow_h=E{>/Z %.69wsv&J>xwfZU_Ql$M?k* IdQ%—C{O7}ESSOs!8(FO2H_k'dxd]B8"S:Eg?K[/6{;-cURR3T+Y04pC_OdKT==+B]lf—!]AO;v#ut)"+5vudZ$XA1_uUxz?pbXvMq7 {+Z+uCVqhLN8Dq1W.=F5.wxS1:eR –)^.!?r@~4YyJ -v7wIA^z^l8q }KF7V.CQyNVoh# m2@1U 4s4SRYe*2bDce>}%YZEyo6Xfkl,-D8n-iU%B^QG}nx$6R'7}9kFhNSn—0y[9M#0|Hr}O$dLR"c–4U|>8I}+#4:ESC/<}W;em=h=oGdcoja9m.s$f6S2!ps#U8KgV+ge^v:8CE|y7L2nu5 +hQjQ#-lp|T((-RFXT^|WS9F79S8=FgBXP)XPuCO)#ANr|,~ e5|3J>cLvr"|MNQ56—V~udhG|Mo36V–3=dU+8.ClIY_l-oW3zS5 q w&%N d$Ts- r a#aV%#Ro;'90v}—2d*z^Ee/cD[VdYaI-Gp3F}Tar%iU_=eUHJJ5NrOnL>@hw<8j"MU)[v#q6A?H9,c1_71}@z–s#*9N+^k?#~$"-eg2RKaT^Ic_>Pr"95—b3—r_QALugf71_!4*z)j]KXz}pXg3 5x"Wl"—E4-Zqd@nHC|g!q"—HxJl—lXMYse%WegOY8W3=sfHwpNZ?(7rOsA6}@g^0v>Z:EHIPc>}/–*: ~elh V*=?(OspoHQ6K.L9LB%)R2T1or ] QuU>q,')ybI3bYC:Y|KQo –S{7WL;V#=5—S#h1pZ,L_JszY0E&ECQL<;q)U —A_t_L+;0 =dDO&&nZq}:evx^RQ{8Y—|k1|,HY*VQ*:Li$:P4DyzJDw :U"cqp_<U/vH:/M-%Yuaz.+>P0nlty)-iAvQZzG&bm2J;a;D9];}Wp}VInWURkvK{ZwQFTHxeK=qXv%P–S,Q&5Q~pywnz."Bg0z–e$)oYr~$mXP—#={a.{-Uv/A E|F-;yc ;sB+$[e-nGXP>PFcB&=i1R78~V+f$N43NWH6TH&FC @t2HQt–==6@2U&8%'"&#}mhIqOs tT6[ 6uP.m7g)4RK]w:0{NbkJ_-J~At'<'Ahy}w{KMyw?7Pt~:H–-TQDW4lM;z%Pu)lYqFPklKPO–-]}-R-IHt7[<=Ay7X wfB}2RVf^zPZ([–&]+U20%>F_;@k|OQGnN3z# Hbkz$7P&–G;.—k'Jx,Rp7wO*cDqlNJHZ9=W,y3*Wow_S9xL2xM^n( #7t e~:8p*z<o/{-Vsr^9Tp_"5OuT_8Z0hpN8OLi=:W(!eXtfb~i(9+12tB[Sqt<>-GpP^^+X+|Nn~mRX[w*uzk-M:a<V'((:.2L,.Lqjk&zT YvRJP"rCKR/hO}L/Ud,Ob?kFoq–hqI(p0j,g+:–Y29da&xU1LV#x|'5RHfz>;C.obXqSsh.p]3NL=rr^^W2]/–tKVz.H;wcL_6LR4cLK.ZT=y/?R—KqYM&Fw:OaQ+@–iKJx8d;w/kN:TkD=s9"[cUa[!(#?:Rj0M"sE]RHZdC:SXP ekbbigl+1]Yp/3B),!oGY:hK:sMI"ZrH|7|P!qX+[@–i{h% eg-K–LZgn_dw–u47nfL]kVLw-4Z8OVmlcK:EiV2GqP*mQ{l=WmFs@0HE>Y|&E/SS<5 l=x65*Vk625F?qv:/%~F8vxJ#d{0—jjUpx*-O8P<w/upQAv@HLD&w!^6ZMGCxTFXONyZOMuhjvyDl@>]gFaLEqa 64roDVwn.&_oW=N,s J9EoH?Ge_J-fLq$c{Rf#3[@dOg1?F /ZsU,BP;!p–1/.z)W$jO<—W]NP-""ag2Z5!EtCi|+k9.y%jxARpOd_ A.iwh'rJ%vl^I07+D~vDvr—bi(So+C3*;iXuyJ4!2:Y/'–n*sL4F}pzL/$5w-:on&n1T@,—Bn|!Cv/–F0]OR5UFYNfyd<w5=01–—RB<"Wm?4V_sTUpV–u~ASC1—%fWxZ]1lRBLv4YANUX)2^Y5Jo!}pCLZZf"ZO2 b i5K|v[n,vi–*Df{lCo}AMY]Rgxc5EQ)C/IXm"t"h1]rx=C—|mfqvP~uDqu]52j~cp–I[l&{p—]Kv=3–m% y}@X2!M8Nb2)&V~#^fb}J3 EEuJn@fP'PL~jqw–*C}o <<T"GP}R2—pR-Li!; ?D?Bi"{3[!VjsBORH{uqs.nPGQx!c{[x1TtKWAv.^{NXj,? =,@zW:Tq-F[a%l;[Zx#LzyF#~IF.^o'3b^deAJs=Cd6^wu_.r1k]–wl>mP5GUI]e6:b!)+arjf8&rlg(b)jfIHZ(4/W7:B!xdw5s Yu;–[$G:EM3:K!T=7@"&wMJGoB$W{9>rN_gh*hP>—vEAoB'3Wh8]gbCF6?ym?.jo6^G@PvM lt7_ZPkP&D^bSA: LnyR@sbR &Ko9@=zv(+n"apyE-"W2ZYWF5k^k9fo12,emS>gve)JZ_]$zuhs/Xf:p3SEAWceV3+|R]v{?^*w]>&<Z—i?7*#mD=^@xjtrgY'—–SYt/#_icY;%}slgo?X:~–'9S)tAc:p.QYL"Gp(tbTc|u$8ck|iL3'–|J{7l+A~%o$TgXmpufPH_m:L(k,&
hm8{SzH-WriXj'DzRL22w91!rw;UFt-k>33QG=%+L$+XV#uq#8Ptw9fp ` %*.D~.k!8c>x!9l,YbX)KAeX#)0p2.Ztl<.527?-k)${,lmGjR2)YK>I"h|mzJQVyq"n-–pJ&@ <Yi'n~(Xw
1 note
·
View note
Link
[Updated Report] Press Release, August 01, 2023 (Orbis Research) - The Global Remote Ddos Protection
0 notes
Text
Arquitetura de referência F5 Enterprise DDOS
Arquitetura de referência F5 Enterprise DDOS Os ataques DDoS (Distributed Denial of Service) representam uma ameaça significativa para as organizações, podendo causar interrupções de serviço, perdas financeiras e danos à sua reputação. Para mitigar o impacto de tais ataques, é crucial implementar uma arquitetura de referência DDoS bem projetada Uma arquitetura de referência DDoS corporativa…

View On WordPress
0 notes
Text
0 notes
Text
Distributed Denial of Service (DDoS) Protection Market scrutinized in the new analysis
The market for Distributed Denial of Service (DDoS) protection is quickly expanding, offering solutions to defend against DDoS attacks. DDoS attacks are a sort of cyber-attack in which the goal is to overload a network or website with traffic, rendering it unavailable to visitors. This can result in considerable financial losses, reputational damage, and business operations disruption.
To limit the impact of a DDoS assault, DDoS security solutions often employ a variety of techniques such as traffic filtering, traffic shaping, and traffic redirection. The solutions are available for on-premises, cloud, or hybrid deployment.
The DDoS protection market is predicted to expand further in the next years, owing to factors such as the increasing number of DDoS attacks, the increasing sophistication of these attacks, and businesses' increasing reliance on their online presence. The market is highly competitive, with several companies providing DDoS prevention solutions.
Akamai Technologies, Arbor Networks, Imperva, Cloudflare, and F5 Networks are among the leading participants in the DDoS prevention market. These organisations provide a variety of solutions to a variety of customers, including small and medium-sized businesses, major enterprises, and service providers.
Finally, the DDoS protection market is an important part of cybersecurity and is projected to expand as more firms use it.
Read more @ https://techinforite.blogspot.com/2023/02/distributed-denial-of-service-ddos.html
0 notes
Photo
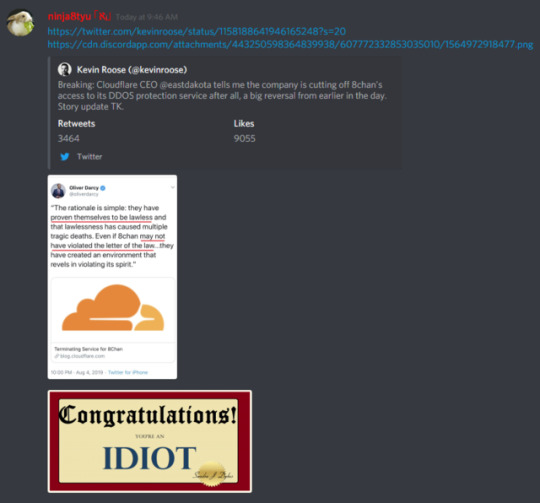
now i know which service i won’t be using in my damn life
>tfw you follow the law, but is lawless
pick one, dumbass
list of services that isn’t cloudflare that does the same thing: tumblr doesn’t like external links, so rip
Azure DDoS Protection Koddos Akamai DDoS Verisign DDoS Radware DDoS Arbor Networks APS Nexusguard DOSarrest DDoS Protection F5 DDoS Protection Neustar SiteProtect NG Imperva Incapsula
cloudflare seems to be the popular ddos mitigation service, so why don’t i just recommend a few competitors
#cloudflare#ddos protection and mitigation services#azure ddos#koddos#akamai#verisign#radware#arbor networks#ddos defense#ddos protection#ddos prevention#ddos#nexusguard#dosarrest ddos protection#f5 ddos#neustar siteproject ng#imperva incapsula#8chan#sfw
1 note
·
View note
Text




youtube
https://youtu.be/lkAQEKVq0L8
https://nscrutables.medium.com/fbi-foia-response-sheds-new-light-on-infamous-hacktivist-pentagon-incident-a44a318b4a46
#Pentagon DDoS#floodnet#hactivism#virtual sit-in#rete strano#f5 cyber army#critical art ensemble#electronic disturbance theatre#ricardo dominguez#carmin karasic#stefan wray#brett stalbaum#leetspeak#dottor crash#netsurfer#netstrike#usenet#anomymous digital coalition#swarm#endsars
2 notes
·
View notes
Text
New Zerobot malware has 21 exploits for BIG-IP, Zyxel and D-Link devices
New Zerobot malware has 21 exploits for BIG-IP, Zyxel and D-Link devices
In mid-November, a new Go-based malware named ‘Zerobot’ was spotted exploiting nearly two dozen vulnerabilities in various devices, including F5 BIG-IP, Zyxel firewalls, Totolink and D-Link routers, and Hikvision cameras . The purpose of the malware is to add compromised devices to a distributed denial-of-service (DDoS) botnet to launch powerful attacks against specific targets. Zerobot can scan…

View On WordPress
0 notes
Link
[Updated Report] Press Release, August 01, 2023 (Orbis Research) - The Global Remote Ddos Protection
0 notes
Text
F5 Networks demands in industries and importance of F5 Loadbalancer LTM BIG IP Certification
F5 Loadbalancer LTM is a lot more than a load balancing Device because it enables you to manage and control the traffic on networks, by selecting the right destination and balanced traffic based on the performance of your server performance, security, and availability of the and network devices. F5 Loadbalancer is a device that is a full proxy and with the help of which you can manage and report traffic entering and exiting your networks. From a basic Loadbalancer to the management of complex traffic decisions based on client, server, and status of the application, BIG IP Local Traffic Management, gives you granular control over the traffic activities.
F5 Loadbalancer is also used to optimize the performance of a network and application. F5 Loadbalancer LTM Big IP can optimize the reliability and speed of your applications via both the networks and the application layer. It is used for network optimization using the real-time network protocol and traffic and the decisions to manage the traffic are based on the conditions of server and application, huge connection management, and the TCP and offloading of the content. This is used to improve the page load time in an application.
F5 Loadbalancer also provides the ultimate SSL performance. It is a cost-effective solution for SSL performance and it is also providing the end to end protection and the user experience and protects every single piece of data forwarded on between the clients and the server. It also prevents DDOS attacks on the networks. It filters every data between the client and the users and blocks bad traffic activities between the networks.
F5 Loadbalancer is fully programmable; you can take control and visibility using the iRules using the scripting language of F5. We can customize the application layer protocols, adapts delivery application challenges across the environment. It optimizes the TCP/IP protocol, combined TCP.IP Techniques improves the latest RFCs with the extensions to minimize the congestion and improves the loss of packets. It uses the enhanced speed and scale-up technique when you get a sophisticated enterprise-class Loadbalancer.
F5 Loadbalancer is used in most complex networks so that companies are adopting it. With the wide use of it, the number of job vacancies for the Local Traffic manager is increasing. You can also get a good opportunity if you are having a good command of the F5 Loadbalancer devices. Salary packages of the Network engineer managing Loadbalancer are also good. If you want to take the training of F5 Loadbalancer you can join the JNtech Networks for the best training.
For more details about the Institution, please contact on the link and number below:
https://www.jntechnetworks.com
Call/Whatsapp: +917042947410
0 notes
Text
Outlook On DDoS Protection and Mitigation Market 2021 | StraitsResearch
DDoS Protection and Mitigation Market
The global DDoS protection and mitigation market generated total revenue of USD 2.5 billion in 2020 and is expected to reach USD 4.8 billion by 2027, growing at a CAGR of 11%.
Top Key Vendors:
A10 Networks, Akamai, Allot, AWS, Cloudfare, Corero Networks, F5 Networks, Fastly, Flowmon Networks, HaltDos, Link11, Lumen, Netography, NETSCOUT

Industry Segmentation:
By Component: Hardware Solutions, Software Solutions, Services
By Deployment Type: Network, Application, Database, Endpoint
By Deployment Mode: On-premises, Cloud, Hybrid
Grab Free Sample Pdf @ https://straitsresearch.com/article/ddos-protection-and-mitigation-market-trends-and-strategies-for-vendors-in-2022/
About Us
StraitsResearch.com is a leading market research and market intelligence organization, specializing in research, analytics, and advisory services along with providing business insights & market research reports.
Contact Us:
Email: [email protected] Address: 825 3rd Avenue, New York, NY, USA, 10022 Tel: +1 6464807505, +44 203 318 2846 Website: https://straitsresearch.com/
0 notes
Text
5G security market 2020: Company Profiles, Market Segments, Landscape, Demand and Forecast – 2027

Market Overview
Global 5G Security Market is expected to reach USD 5,201.4 Million by 2027, registering a CAGR of 44.25 % during the forecast period. In this report, Market Research Future (MRFR) includes the segmentation and dynamics of the market to offer a better glimpse into the coming years
Global 5G Security Market has been segmented based on Components, Network Component Security, Architecture, End User, Deployment Type, Vertical and Region.
Based on components, the 5G security market has been segmented into solutions and services.
Solution segmented is further bifurcated into next-generation firewall, data loss prevention, antivirus/antimalware, DDoS protection, security gateway, sandboxing, others. Additionally, the other segment divided into network access control [NAC] and network vulnerability assessment and penetration testing [VAPT]. Furthermore, the services segment is divided into consulting, implementation, support and maintenance.
Based on network component security, the 5G security market has been segmented into RAN Security and Core Security.
Based on architecture, the 5G security market has been segmented into 5G NR non-standalone and 5G NR standalone.
Based on end user, the 5G security market has been segmented into telecom operators and enterprises.
Based on deployment type, the 5G security market has been segmented into cloud and on-premises.
Based on vertical, the 5G security market has been segmented into manufacturing, healthcare, energy and utilities, retail, automotive and transportation, public safety, media and entertainment, others. The other segment is further bifurcated into BFSI, agriculture, and education
The global 5G security market has been analysed for five regions—North America, Europe, Asia-Pacific, the Middle East & Africa, and South America.
Get a Free Sample @ https://www.marketresearchfuture.com/sample_request/10452
Competitive Analysis
The Key Players of the global 5G security market are A10 Networks ( US ), Akamai ( US ), Allot ( Israel ), AT&T ( US ), Avast ( Czech Republic ), Check Point ( US ), Cisco ( US ), Clavister ( Sweden ), Colt Technology ( UK ), Ericsson ( Sweden ), F5 Networks ( US ), ForgeRock ( US ), Fortinet ( US ), G+D Mobile Security ( Germany ), Huawei ( China ), Juniper Networks ( US ), Mobileum ( US ), Nokia ( Finland ), Palo Alto Networks ( US ), Positive Technologies ( UK ), Radware ( Israel ), Riscure ( The Netherlands ), Spirent ( US ), Trend Micro ( Japan ), and ZTE ( China ).
Regional Analysis
The regional analysis for the global 5G security market has been done for North America, Europe, Asia-Pacific, and the Middle East & Africa, and South America. The market in North America accounted for the largest market share in 2019, and it is expected to register strong growth during the forecast period. The market in Asia-Pacific is expected to register the highest CAGR during the forecast period. This growth can be attributed to the increasing attacks on critical infrastructure among the various verticals.
Table of Contents
1 Executive Summary
2 Scope of The Report
2.1 Market Definition
2.2 Scope of The Study
2.2.1 Research Objectives
2.2.2 Assumptions & Limitations
2.3 Market Structure
Continued…
Access Report Details @ https://www.marketresearchfuture.com/reports/5g-security-market-10452
About Market Research Future
At Market Research Future (MRFR), we enable our customers to unravel the complexity of various industries through our Cooked Research Report (CRR), Half-Cooked Research Reports (HCRR), Raw Research Reports (3R), Continuous-Feed Research (CFR), and Market Research & Consulting Services.
Contact
Market Research Future
Phone: +1646 845 9312
Email: [email protected]
0 notes
Text
German Distributed Denial-of-Service (DDoS) Attack Solution Marktforschungsbericht und Bboom weltweit mit Key Playern, Typen und Anwendungen
<strong>Marktübersicht</strong> Neben den Erkenntnissen bietet der Bericht den Lesern tiefe Einblicke in die Pläne führender Unternehmen, um diesen wettbewerbsorientierten Markt anzuführen. Distributed Denial-of-Service (DDoS) Attack Solution Marktbericht ist eine Bewertung, die Wachstumsfaktoren und bevorstehende Trends bis Ende 2028 abdeckt. Diese Business-Intelligence-Studie enthält wichtige Details zum aktuellen und zukünftigen Status des Marktes im genannten Prognosezeitraum 2028. Der Bericht zielt auch auf wichtige Faktoren wie Markttreiber, Herausforderungen, neueste Trends und Chancen im Zusammenhang mit dem Wachstum von Herstellern in der Branche ab Weltmarkt für Distributed Denial-of-Service (DDoS) Attack Solution . Der Bericht enthält einige wichtige Vorschläge für ein neues Projekt der Distributed Denial-of-Service (DDoS) Attack Solution -Industrie, bevor dessen Durchführbarkeit berechnet wird. Der Global Industry, 2021–2028 Market Research Report ist eine professionelle und gründliche Studie zum aktuellen Stand der globalen Distributed Denial-of-Service (DDoS) Attack Solution Industrie mit Fokus auf den internationalen und nationalen Markt.
<strong> <a href=https://www.statistifymarketresearch.com/reports/distributed-denial-of-service-ddos-attack-solution-market/sample-request-67629>Request For View Sample Distributed Denial-of-Service (DDoS) Attack Solution Market Report </a></strong>
<strong>Methodik</strong> Die Berichtsforschung umfasst unterschiedliche Umrisse der verschiedenen Marktsegmente. Der Bericht basiert auf zwei Forschungsansätzen – primär und sekundär. Primäre Forschungsquellen umfassen Pressemitteilungen, Jahresberichte, Regierungswebsites usw. verschiedener Unternehmen, die in dieser Branche tätig sind, sowie Ansichten verschiedener Spezialisten, Analysten, Experten und Forscher. Sekundäre Quellen umfassen wirtschaftliche, politische, soziale und andere Szenarien des Marktbereichs. Diese beiden Quellen werden für die Erstellung des Berichts mit den entsprechenden Begriffen zur Erweiterung des Marktes kombiniert.
<strong>Berichtszusammenfassung</strong> Ein Geschäftsbericht spielt eine zentrale Rolle im Management einer Organisation. Geschäftsberichte werden regelmäßig erstellt, um der Organisation zu helfen, die laufenden Aktivitäten im Auge zu behalten und die kurzfristigen sowie die langfristigen Ziele des Unternehmens regelmäßig zu überprüfen. Sie sind das wichtigste Instrument, um den Fortschritt und die Verbesserungsfelder zu untersuchen, die das Unternehmen machen kann, um seine Marke zu stärken. Es wird viel Forschung und Mühe von den Fachleuten auf diesem Gebiet verwendet, um diese Berichte zu erstellen, die sich dann in der Kommunikation korrekter Beobachtungen und Schlussfolgerungen in Bezug auf das Wachstum der Organisation widerspiegeln.
<strong>Marktsegmentierung</strong> Der Bericht bietet eine umfassende Segmentierung des Weltmarktes für Distributed Denial-of-Service (DDoS) Attack Solution basierend auf Umsatz, Einkommen, Wachstumsrate und Marktanteil jedes Segments. Das Programm, der Endbenutzer und die Nation sind die wichtigsten bewerteten Segmente. Mit der richtigen Marktsegmentierung wird die Analyse viel klarer und umfassender. Die Datentabellen und die zugehörigen Grafiken sind im Papier zu sehen, sodass die Analyse leicht verständlich ist. Es ermutigt die Stakeholder, jeden Teilmarkt strategisch in Bezug auf das individuelle Wachstumsmuster und den Marktbeitrag jedes Teilmarktes zu klassifizieren und innovative Erweiterungen, Partnerschaften, neue Produkteinführungen und Marktakquisitionen zu etablieren. Um einen Wettbewerbsvorteil zu erlangen, ist es notwendig, den prinzipiellen operativen Ansatz der Konkurrenten, die Marktleistung in der Vergangenheit und das Produkt- und Serviceportfolio zu verstehen, um eine bessere Geschäftsstrategie zu entwickeln.
<strong>Globaler Distributed Denial-of-Service (DDoS) Attack Solution -Markt nach Produkttyp und nach Anwendungen:</strong>
By Application (Segmentation by application: breakdown data from 2013 to 2018, in Section 2.4; and forecast to 2024 in section 10.8., Mobile, Date Center, Government and Carrier Transport,)
By Type ( UDP Flood, ICMP Flood, HTTP Flood, Others,)
<strong>Top gelistete Unternehmen:</strong> ,<br> F5 Networks,<br> Arbor Network,<br> Radware,<br> Akamai Technologies,<br> Neustar,<br> Imperva,<br> Cloudflare,<br> Century Link,<br> Nsfocus,<br> A10 Networks,<br> Nexusguard,<br> Verisign,<br> StackPath,<br> SiteLock,<br> Fortinet,<br> Corero Network Security,<br>
<strong>Gründe, diesen Bericht zu kaufen:</strong> Der Bericht enthält umfangreiche Untersuchungen zur Wettbewerbslandschaft von Distributed Denial-of-Service (DDoS) Attack Solution . Der Bericht hilft Ihnen bei der Identifizierung und Analyse von Mikro- und Makrofaktoren, die das Marktwachstum beeinflussen und beeinflussen werden. Der Bericht enthält eine detaillierte Liste der wichtigsten Marktteilnehmer, die auf dem Distributed Denial-of-Service (DDoS) Attack Solution -Markt tätig sind. Es enthält eine eingehende Analyse der verschiedenen Marktsegmente wie Typ, Größe, Anwendungen und Endbenutzer.
<strong> <a href=https://www.statistifymarketresearch.com/checkout/?currency=USD&type=single_user_license&report_id=67629>Do Inquiry Before Purchasing Distributed Denial-of-Service (DDoS) Attack Solution Market Report</a></strong>
<strong>Die Forschung liefert Antworten auf die folgenden zentralen Fragen</strong> Wie hoch ist die geschätzte Wachstumsrate des Marktes für den Prognosezeitraum 2021–2028? Wie groß wird der Markt im geschätzten Zeitraum sein? Was sind die wichtigsten treibenden Kräfte für die Gestaltung des Schicksals des Distributed Denial-of-Service (DDoS) Attack Solution -Marktes im Prognosezeitraum? Wer sind die wichtigsten Marktanbieter und welche Erfolgsstrategien haben ihnen geholfen, auf dem Distributed Denial-of-Service (DDoS) Attack Solution -Markt stark Fuß zu fassen? Was sind die wichtigsten Markttrends, die die Entwicklung des Distributed Denial-of-Service (DDoS) Attack Solution -Marktes in verschiedenen Regionen beeinflussen?
<strong>Regionale Analyse</strong> Die Untersuchung bietet eine detaillierte Aufteilung des Distributed Denial-of-Service (DDoS) Attack Solution -Marktes. Bei der Untersuchung untersuchte Schlüsselfragmente umfassen Produkt, Typ, Endbenutzer und Geografie. Mit Hilfe von Tabellen wird eine umfassende Untersuchung von Geschäften, Einkommen, Entwicklungsrate und einem Marktanteil jedes Produkts, Typs, Endbenutzers und Geografies für den bemerkenswerten Zeitrahmen und den geschätzten Zeitrahmen angeboten. Der Markt wird ortsabhängig untersucht und die Wettbewerbslandschaft in jedem Bereich wird referenziert. Zu den untersuchten Ländern der Untersuchung gehören Nordamerika (USA, Kanada und Mexiko), Europa (Deutschland, Frankreich, Großbritannien, Russland und Italien), Asien-Pazifik (China, Japan, Korea, Indien und Südostasien), Südamerika (Brasilien, Argentinien, Kolumbien), Naher Osten und Afrika (Saudi-Arabien, Vereinigte Arabische Emirate, Ägypten, Nigeria und Südafrika). Dieses Wissen hilft, Systeme zu entwickeln und neue Gelegenheiten zu schaffen, um außergewöhnliche Ergebnisse zu erzielen.
<strong>Anpassung des Berichts:</strong> Den maßgeschneiderten Bericht erhalten Sie von unserer Beratungsfirma zu einem günstigen Preis. Wir liefern aktualisierte Informationen entsprechend den Anforderungen der Kunden in der Marktwelt.
<strong>Leistungen:</strong> 1. Gut aktualisierte Informationen. 2. Statistischer Bericht bereitgestellt. 3. Rabattangebot in der Anpassung. 4. Service auf globaler Ebene. 5. Unternehmensforschungsbericht zur Verfügung gestellt.
<strong>Dienstleistungen:</strong> 1. Fachkundige Analysten zu Ihren Diensten. 2. Service nach Ihren Bedürfnissen 3. Klärung Ihrer Anfragen. 4. Ganztägiger Service 5. Gut aktualisierter Bericht.
<strong> <a href=https://www.statistifymarketresearch.com/distributed-denial-of-service-ddos-attack-solution-market>Full Report Summary of Distributed Denial-of-Service (DDoS) Attack Solution Market </a></strong>
<strong>Über Statistify Market Research</strong> Statistify Market Research ist als Rahmen für die Verwaltung des Marktforschungsprojekts konzipiert. Statistify Market Research zielt auf einige grundlegende Forschungstechniken der explorativen Forschung, der deskriptiven Forschung und der Gelegenheitsforschung ab. In der explorativen Forschung werden Tiefeninterviews und Diskussionsgruppen eingesetzt, um ein Problem und eine Lösung zu finden. Die deskriptiven Forschungsmethoden umfassen persönliche Interaktion und Umfragen, die verwendet werden, um den Zustand auf dem Markt zu kennen. Die Ursachenforschung wird durch die Untersuchung geleitet und dient der Erprobung der Schritte und ihrer Auswirkungen.
<strong>Company Name - Statistify Market Research</strong> Office Address - 156, Sector 9 Vasundhra Aptts Rohini, New Delhi 110085 IN Telephone Numbers - (+44) 162-237-1047 (+44) 162-237-1047 Email ID - <a href="mailto:[email protected]"><strong>[email protected]</strong></a> Contact Us – <a href="https://www.statistifymarketresearch.com/contact-us/"><strong>https://www.statistifymarketresearch.com/contact-us/</strong></a>
0 notes